A handful of nice machining manufacturer images I identified:
Image from web page 16 of “Scientific American Volume 85 Quantity 01 (July 1901)” (1901)

Image by Web Archive Book Images
Identifier: scientific-american-1901-07-06
Title: Scientific American Volume 85 Quantity 01 (July 1901)
Year: 1901 (1900s)
Authors:
Subjects: gas railroad munn cents steam companies american electric scientific american natural gas sheet metal sewing machine ten cents american supplement lengthy island soft coal cubic feet bituminous coal
Publisher:
View Book Page: Book Viewer
About This Book: Catalog Entry
View All Pictures: All Photos From Book
Click here to view book on-line to see this illustration in context in a browseable on the internet version of this book.
Text Appearing Before Image:
preferred, andremit to Mniui & Co.. Sfil Broadway, New York. Canadian patents may now be obtained by the in-vontnrs for auy of the inventions named in the fore-going list. For terms and additional particularsaddress Mans & Qo,, 361 Broadwafi New Xork. By GEORGE M. HOPKINS. 20th Edition Revised and Enlarged. 914 Fagres, 820 Illustrations. Price tag .00 In cloth .00 In half morocco, postpaid Thi.s is a book full ofinterest and value lorTeachers, Students,and others who desireto impart or acquire apractical expertise ofPhysics. Ihis splendidwork offers young andold something worthyof thought. It has in-fluenced thousands ofmen in tbe option of acareer. It will give any-a single, young or old, in-formation that will en-in a position him to compre-hend the excellent im-provements 01 the day.It furnishes sugges-tions for hours of in-structive recreation. ISend for lar^e Illustrated Circularand full Table of Couteuts. Munn & Co., Publishers, Workplace of the SCIENTIFIC AMERICAN,361 BROADWAY. NEW YORK.
Text Appearing Following Image:
ELECTRICAL ENCINEERINCTAUCHT BY MAIL. Write for our Cost-free Illustrated Book. CAN I Grow to be AN ELEC-TRICAL ENGINEER? We tr.Hi-h Elfvtrtciil Kngineering, El«-ttnr Liglitms,Electrii Railways, KlechHiiioal Engineerintr Sttjaiii Eiii^iiieeriiig, Mechanical Drawing, at voiir luiiiir by mail.Institute iTuiorst-.l hv Tlios. A. F.dison ami othtrS.ELECTItl C A1/ KN ( I N KK li IN KTITUTE,Dei»t. A, a4«-a4a W. a»d Nt.. Now York. 7 ANTED, DRA.FrSMAN.-A COMPETITIVE EX- amination of applicants will be held at the NavyYard, Norfolk, Va., July 16, 19(11, for structural steelwork draftsman at ?l,5(ii per annum. For applicationand added data, address (Commandant,Navy Yard, ^Tnrfolk, Va. JOHN D. Long, Secretary of the Navy.
Note About Images
Please note that these pictures are extracted from scanned web page images that may have been digitally enhanced for readability – coloration and appearance of these illustrations might not perfectly resemble the original function.
Image from web page 14 of “Scientific American Volume 85 Number 01 (July 1901)” (1901)
Image by World wide web Archive Book Pictures
Identifier: scientific-american-1901-07-06
Title: Scientific American Volume 85 Quantity 01 (July 1901)
Year: 1901 (1900s)
Authors:
Subjects: gas railroad munn cents steam companies american electric scientific american all-natural gas sheet metal sewing machine ten cents american supplement lengthy island soft coal cubic feet bituminous coal
Publisher:
View Book Page: Book Viewer
About This Book: Catalog Entry
View All Images: All Images From Book
Click here to view book online to see this illustration in context in a browseable on the internet version of this book.
Text Appearing Prior to Image:
hld, Pape & Witter. 677,203Oven for baking, roasting, and so forth., Bram- mertz & Fausten 077,173 (Continued on poye U) n- IF YOU ARE Creating ^• AN AUTOMOBILE.WECAN Supply YOUWITH PARTSandTITTINCS. , jIN OUR SEVEN FACTORIES we make. Running.GLAR5, TOOL SJLLL BALuS,STEEL RIMS, STEEL STAMPINGS, CKAIN.S, SHEET STEEL AND FORCINGS.ALL FOR AUTOMOBILE. Building CS,UOTATIONS • ON APPLICATION. THE AUTOMOBILE & CYCLE Parts CO. ,-. ^ ,,,^ , » ,..,-, OHIO. METAL POLISHES.—FORMULAS FOR Putz Pomades, Pastes, Liquicis, Fowdersand Soaps,forpolishing metals, are contained in Scientific Ameri-can Supplement Noa. l!i8:i, I^SS and l28!l.Price ten cents eacb, trom this office and all newsdealers. YOUR BICYCLM Might require a new crank haneer or greater gear. We canfurnish crank hangers comprehensive with cups and cones,to match any wheel. Create us for full data.The Avery & Jenness Co., 60 S. Canal St., Chicago, III. INDUCTION w vj i L> ^ for experi-ments in X rays andother electrical work.
Text Appearing Soon after Image:
Catalogue Fixe. E. S. RITCHIE & SONS, Brooklinc. Mass.
Note About Images
Please note that these photos are extracted from scanned web page photos that could have been digitally enhanced for readability – coloration and look of these illustrations could not completely resemble the original work.
Image from web page 6 of “Scientific American Volume 85 Quantity 01 (July 1901)” (1901)
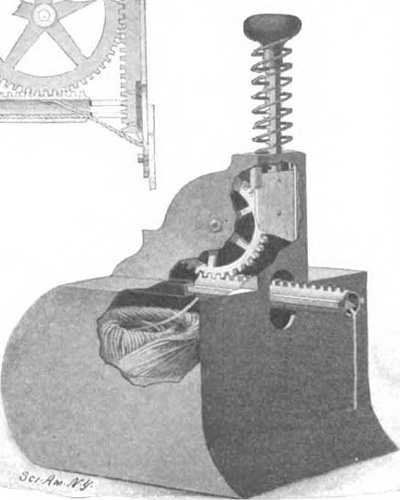
Image by Web Archive Book Pictures
Identifier: scientific-american-1901-07-06
Title: Scientific American Volume 85 Number 01 (July 1901)
Year: 1901 (1900s)
Authors:
Subjects: gas railroad munn cents steam producers american electric scientific american all-natural gas sheet metal sewing machine ten cents american supplement extended island soft coal cubic feet bituminous coal
Publisher:
View Book Web page: Book Viewer
About This Book: Catalog Entry
View All Images: All Images From Book
Click right here to view book on-line to see this illustration in context in a browseable on the internet version of this book.
Text Appearing Just before Image:
e at alighthouse at Grande Polnte au Sable, in Michigan,says The Architect. The lighthouse, which is about80 feet high, is formed of brick with a stone base. Itwas erected in 1867, but nearly from its completion ithas suffered from the violent rain storms of the dis-trict. For a long time pointing was undertaken regu-larly, but at length it was determined to Incase thelighthouse with metal. The bent plates used varierl A NOVEL TWINE HOLDEB AND CUTTEB. A device which is specially adapted for guiding andcutting twine to be utilized in tying up packages has re-cently been patented in the Uplted States by RaymondD. Weakley, of St. Louis, Mo. As our illustration shows, the device comprisesessentially a lower compartment and an upper com-partment, the former of which contains the ball oftwine and the upper of which incloses the operativemechanism. This operative mechanism comprises a toothedwheel meshing with a rack formed on a carrier. Thecarrier is tubular in type and receives the cost-free end of
Text Appearing After Image:
Note About Images
Please note that these photos are extracted from scanned web page photos that may possibly have been digitally enhanced for readability – coloration and appearance of these illustrations might not completely resemble the original operate.



